THOUGHT LEADERSHIP
Insights on best practice and inclusivity in cybersecurity.

🚨 Cybersecurity Alert: New Insights from Microsoft's MTAC-East Asia Report (April 2024)🚨
The "MTAC-East Asia Report" by Microsoft Threat Intelligence, published in April 2024, provides an in-depth analysis of cyber and influence operations conducted by East Asian actors, particularly focusing on China and North Korea and the use of AI. This post is structured to give insights into:
• the methods,
• targets, and
• strategic implications of these activities.

AISec Case Study - Compromised PyTorch Dependency Chain
In a striking breach of security, malicious binaries masquerading as PyTorch dependencies compromised sensitive data on numerous Linux systems through PyPI, unveiling the dangers of dependency confusion in software supply chains.

AI Security Case Study - Bypassing ID.me AI identity Verification - costing $3.4 million.
An individual in California exploited ID.me's identity verification flaws to file 180 fraudulent unemployment claims, obtaining over $3.4 million by using fake IDs and wigs for false verifications, and was eventually sentenced to nearly seven years for wire fraud and aggravated identity theft.


Introducing KATO AI - Kaze’s Decision Engineering Platform
KATO AI is Kaze’s Decision Engineering platform that enables the development of our human-machine teaming products and services - using our Decision Science, Data Science and AI capabilities we remove uncertainty for business leaders, enabling them to make decisions with confidence.

AI Security Case Study - Deepfake results in the theft of $77 million
This case study provides an example of where an AI Security vulnerability was exploited at a cost of $77 million to a government organisation.

AI Security (AISec) - A Threat Capability Matrix
Threat Capability Matrix - An approach to separate fear from reality in AI Security.


Useful Resources for AI Security
Don’t become a victim!
A useful set of tools and reference guides to help you secure your organisations AI value from cyberattacks.
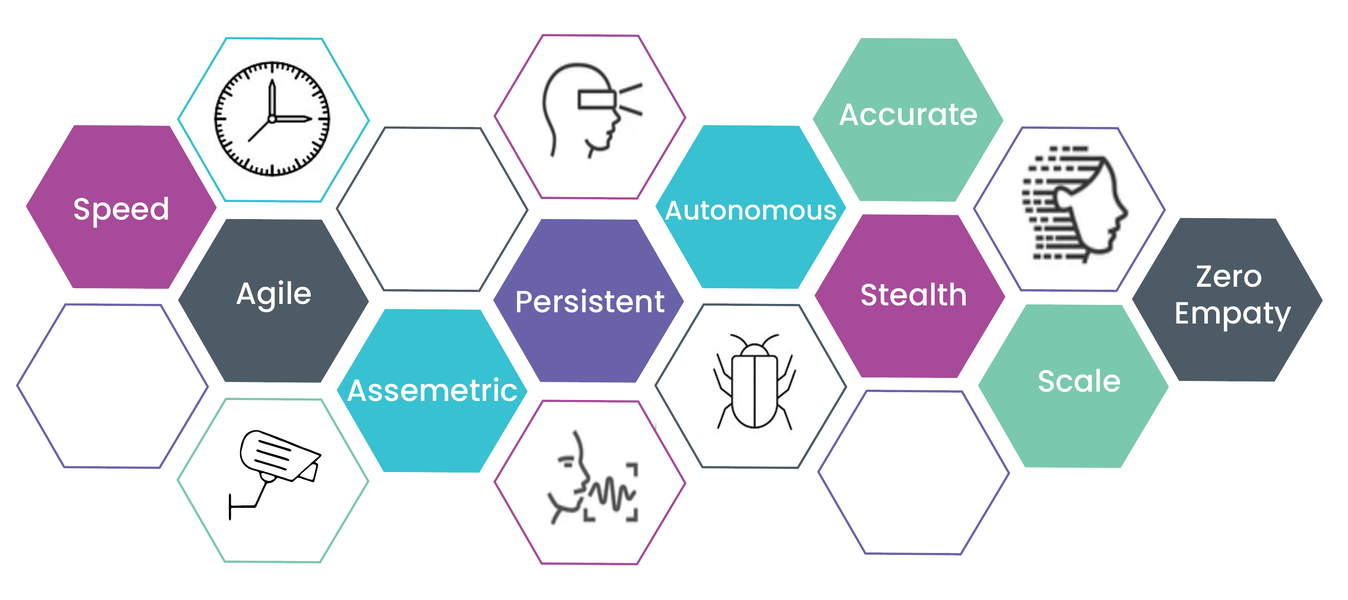
Characteristics of a future AI enabled cyberattack
In an era where the cyber threats become the number one risk for organisations, the National Cyber Resilience Centre (NCRC) issues a stark warning: AI is set to amplify the scale and impact of cyberattacks, enabling a broader spectrum of malicious actors.

Reference Architecture for an AI Cyber Agent
The rapid evolution of cyber threats and the increasing complexity of digital ecosystems have underscored the need for advanced cybersecurity measures. Intelligent agents will emerge as a promising approach for addressing these challenges, leveraging AI and machine learning techniques to detect and mitigate cyber threats in real-time. However, the design and deployment of effective agent-based solutions require a structured approach to ensure scalability, interoperability, and adaptability across diverse environments.
Get in Touch
Reach out with any questions or inquiries, and James will provide the strategic solutions you need.
